Ieee Papers On Cryptography And Network Security Pdf - On other hand network security is the process of keeping the information private secret and secure from unauthorized and illegal access. Cryptography and network security is.

Pdf Review And Open Issues Of Cryptographic Algorithms In Cyber Security
Security in Cloud Computing using Cryptographic Algorithms Miss Shakeeba S.

Ieee papers on cryptography and network security pdf. In this paper we describe some of the recent research going on in the field of cryptography and network. The experimental results suggest that the RSA and AES hybrid encryption algorithm can not only encrypt files but also provide the benefits of efficiency and protection of the algorithm. A high performance substitution box S-Box FPGA implementation using Galois Field GF 28 is presented in this paper.
Online Study Material Lecturing Notes. However a general overview of network security and cryptography. IEEE Network Security Cryptographic Sciences projects for MTech BTech BE MS MCA BCA Students.
In particular we propose a novel Source Authentication using Network Coding SANC scheme. From this unique key a random sequence is generated which is used as an asymmetric key for both Encryption and Decryption. Abstract-This paper aims to provide broad view of usage of cryptography in network security.
Some of the recent research going on in the field of cryptography and network security are described and the main motivation behind each research paper is explained and the proposed solution is stated briefly in light of brevity. In this paper we. Discussion of these research.
Cryptography and Network Security - Question Bank 3 - Download Pdf Cryptography and Network Security - 2 marks with answers 1 - Download Pdf. May 18 2003 posted here 11903 The first MiAn International Conference on Applied Cryptography and Network Security ACNS03 will be held in Kunming China on October 16-19 2003 organized. CRYPTOGRAPHY-2020-RESEARCH TECHNOLOGIES IEEE PROJECTS PAPERS.
Many people use cryptography on a daily basis not everyone is aware of it. The encryption process consists of an algorithm and a key. IT2352 CRYPTOGRAPHY AND NETWORK SECURITY SCE DEPARTMENT OF INFORMATION TECHNOLOGY nonsense referred to as cipher text.
This paper investigates the applications of cryptography in the context of databases and offers suggestions to enhance security and privacy. Demonstrated a review of some of the research that has been. Principles and Practices Sixth Edition by William Stallings HANDBOOK Handbook of Applied Cryptography Fifth Printing by Alfred J.
Plain Text and Cipher. Our research paper writing service is rated 84910 based on 517 reviews. Aim of cryptography is to take care of data secure from invaders.
2021 IEEE International IOT Electronics and Mechatronics Conference IEMTRONICS. Open key encryption in which message is scrambled with a beneficiarys open key. They are Symmetric-key encryption A symmetric-key encryption and Hash functions.
Cloud Computing is a set of IT Services for example network software system storage hardware software and resources and these services are provided to a customer over a network. Submissions with main contribution in other areas such as information security software security system security or applied cryptography will. CSE Seminars 1 Comment.
Because of that the security issue of RFID is becoming more important. Cryptography and Network Security - CS8792 CS6701. In this paper we describe some of the recent research going on in the field of cryptography and network security.
CRYPTOGRAPHY AND NETWORK SECURITY BCS- 3-0-1 Credit-4 Module I 12 LECTURES Introduction to the Concepts of Security. Stinson CRC Press Taylor and Francis Group References CR 26 STALLINGS Cryptography and Network Security. There are three key process techniques.
ACNS03 First MiAn International Conference on Applied Cryptography and Network Security Kunming China October 16-19 2003Extended deadline. These commonly available security products need to be upgraded with quantum safe cryptographic techniques and this paper explores some of the most pervasive security systems while giving practical recommendations for upgrading to a quantum safe state. Theory and Practice Third Edition by Douglas R.
CRYPTOGRAPHY IEEE PAPER 2018. Cryptography or cryptology from Ancient Greek. The main aim of this paper is to provide a broad review of network security and cryptography with particular regard to digital signatures.
The work requirements of for example a. CITL Tech Varsity Bangalore Offers Project Training in IEEE 2021 Network Security Cryptographic Sciences. These focuses are encryption and unscrambling time and throughput at both encryption and decoding sides 5.
The need for security Security Approaches Principles of Security Types of Attacks. A hybrid encryption algorithm mixing AES and RSA algorithms is suggested in this paper to overcome the above issues in order to solve file encryption performance and security problems. Cryptography and Network Security Seminar and PPT with PDF Report.
We are providing here Cryptography and Network Security Seminar and PPT with pdf report. Component of broader network security products. Changing the key changes the output of the.
The key is a value independent of the plaintext. Cryptography has the importa nt purpose of providing reliabl e strong and robust netw ork and data security. Network security and cryptography is a subject too wide ranging to coverage about how to protect information in digital form and to provide security services.
ABSTRACT RFID is a wireless technology for automatic identification and data capture and its the core technology to implement the internet of things. If you need an article that corresponds to your case studies in Research Paper On Cryptography And Network Security Pdf a particular field and there are difficulties with translation only specialists from can solve this problem. In this paper we explore the security merits of network coding and potential trade-offs with the widely accepted throughput benefits especially in multicast scenarios.
We propose a biometrics-based fingerprintEncryption Decryption Scheme in which unique key is generated using partial portion of combined senders and receivers fingerprints. Of CSE BMSCE Bangalore India ABSTRACT. A Review paper on Network Security and Cryptography 769 systems on two focuses.
Accepted and presented papers will be published in the IEEE 2015. A Survey of Authentication of RFID Devices Using Elliptic Curve Cryptography. IEEE 80211i Wireless LAN Security Wireless Application Protocol Overview.
And γράφειν graphein to write or -λογία -logia study respectively is the practice and study of techniques for secure communication in the presence of third parties called adversaries. Cryptography is defined as the science of protecting the data. Topics of interest encompass all practical and theoretical aspects of communications and network security.
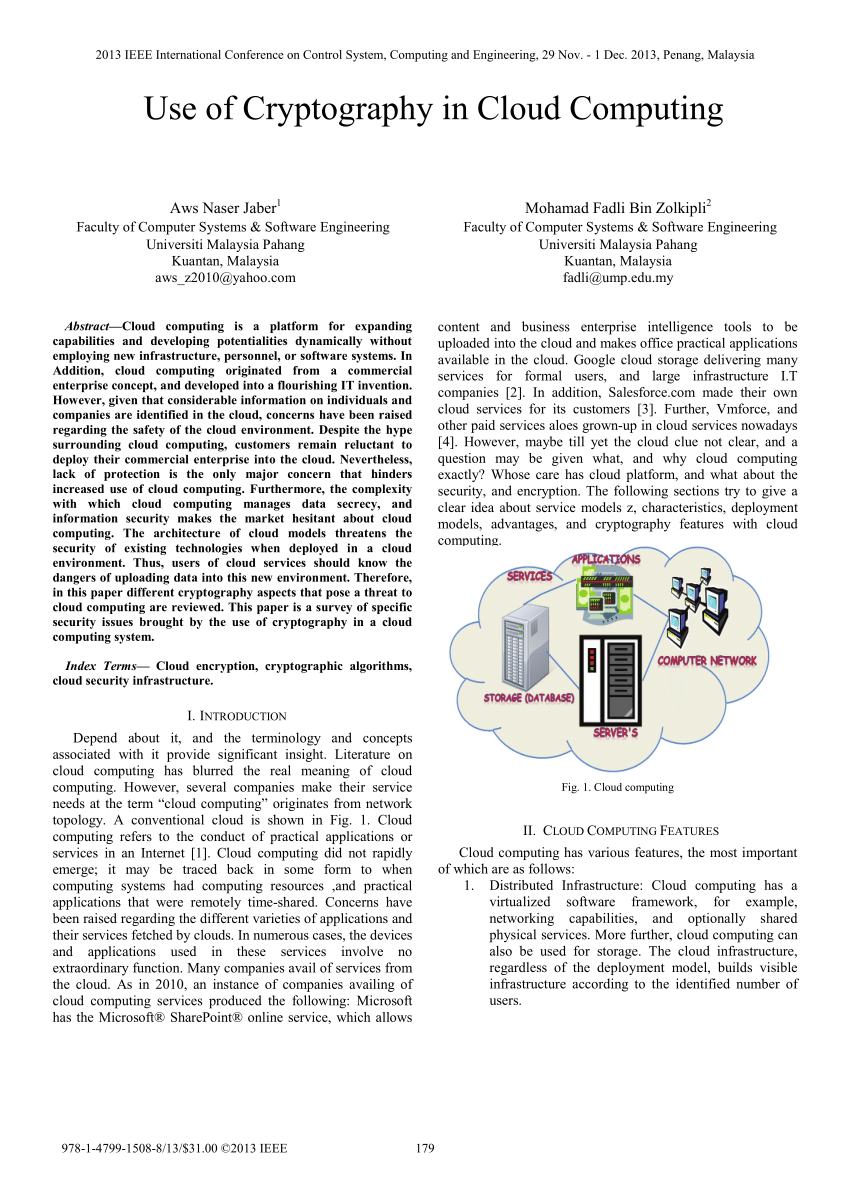
Pdf Use Of Cryptography In Cloud Computing

Pdf Passive Security Threats And Consequences In Ieee 802 11 Wireless Mesh Networks

Pdf Cryptography Network Security Hash Function Applications Attacks And Advances A Review

Pdf The Design Of A Cryptography Based Secure File System
Ieee Papers On Network Security Pdf Wireless Sensor Network Encryption

Pdf Cryptography Security Future Challenges And Issues

Pdf A Review Paper On Cryptography

Pdf A Survey On Network Security And Cryptography

Pdf Data Security And Integrity In Cloud Computing Based On Rsa Partial Homomorphic And Md5 Cryptography
Gacbe Ac In

Pdf Network Security A Brief Overview Of Evolving Strategies And Challenges

Pdf A Review On Lightweight Cryptography Algorithms For Data Security And Authentication In Iots

Pdf Network Security With Cryptography
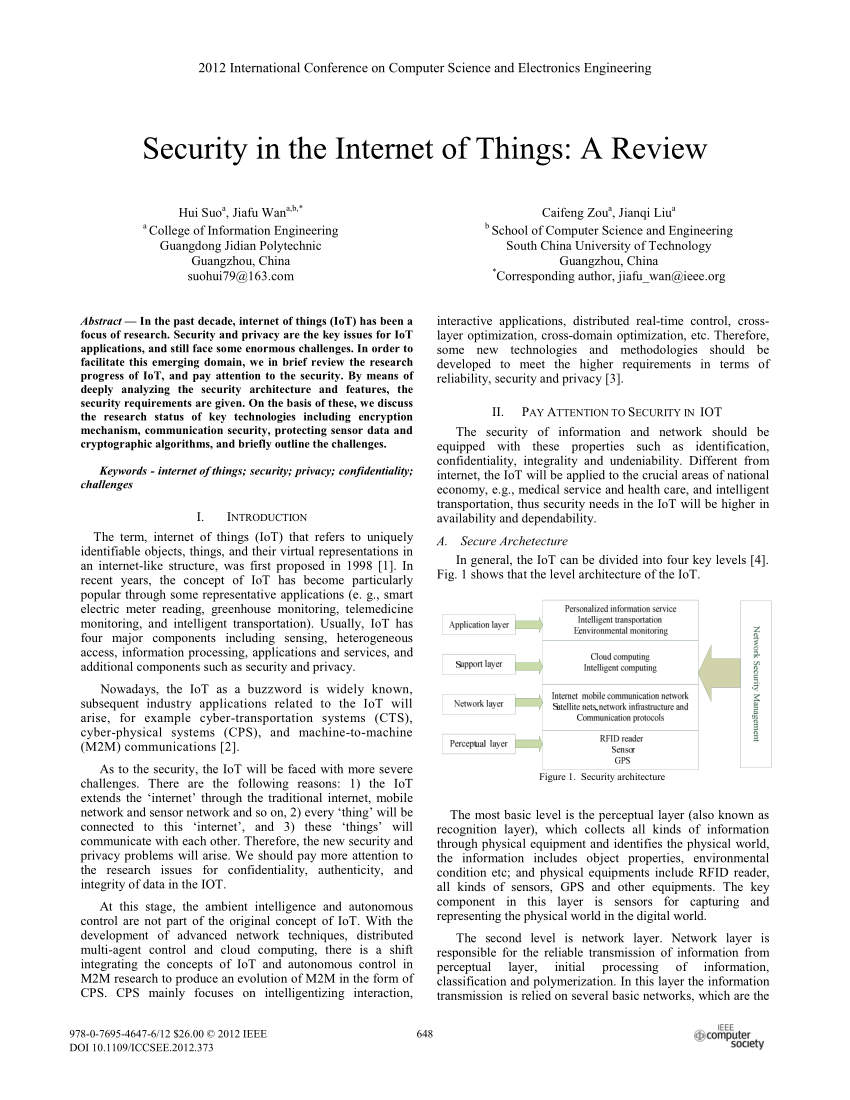
Pdf Security In The Internet Of Things A Review
